WordPress Permissions – How To Set Up Proper Filesystems And Ownerships
When people talk about WordPress security, file permissions and ownership are usually the last thing on their minds. Installing security plugins is a good practice and a must for every WordPress website. However, if your file-system permissions aren’t set up correctly, most of your security measures could be easily bypassed by intruders.

Permissions and ownership are quite important in WordPress installations. Setting these up properly on your Web server should be the first thing you do after installing WordPress. Having the wrong set of permissions could cause fatal errors that stop your website dead. Wrong permissions can also compromise your website and make it prone to attacks.
Aside from the security concerns, a number of other issues can stem from having the wrong set of permissions and ownership. Have you ever encountered a blank white screen when trying to load your website for the first time? Or have you ever received error messages when trying to upload images in the media uploader? Correcting permissions and ownership of your files and folders will often fix these types of problems.
In this article, we will teach you all about WordPress filesystem permissions and ownership: what they are, why they are important and how to set them up. You will learn a few basic principles that I follow to keep my file system intact. We will also cover the two most common WordPress server configurations. We’ll explain how they differ and, more importantly, how to set the proper permissions and ownership for each.
Terminal Vs. FTP Client
During the course of this article, we will be using the terminal to change permissions and ownership. Why not use an FTP client instead? The reason is that FTP is a bit limited for our needs. FTP can be used to transfer files and change file and folder permissions, but it cannot be used to change ownership settings.
To perform the commands listed in this article, you will have to be logged into your server using the SSH command. If you are not familiar with the terminal and SSH, you can learn about them in the article “Introduction to Linux Commands.”
Users And Groups
Before anything else, we need to quickly talk about what users and groups are, because these go hand in hand when defining permissions.
To put it simply, a user is an account that has access to the computer, and a group just is an identifier for a certain set of users. This means that every time you transfer files using FTP, you are using a user account on your server. And depending on how your host has set up your account, you (the user) might belong to one or more groups. Users and groups are like users and roles in WordPress. Both are conceptually the same, except that the former is used on your server.
Users and groups are important because they help to identify privileges for all of our files and folders. Owners of a file normally would have full privileges on it; other users who belong to the same group would have fewer privileges on it; while everyone else might have no privileges on it. These privileges are what we call permissions.
What Are File Permissions?
Permissions dictate what users can do with a file. A permission is represented by a set of numbers, such as 644 or 777, referred to as a permission mode. If you have used plugins in WordPress before, then you’ve most likely been asked by some of them to change the permissions of a file or directory because the plugin can’t write to it. By changing the file’s permissions, you are allowing the Web server to gain access to that file or folder.
Think of a permission mode as a set of “who can do what” statements, in which each digit corresponds to the “who” part of the statement:
- First digit. What the user of the account that owns the file can do
- Second digit. What other user accounts in the owner’s group can do
- Third digit. What the user accounts of everyone else (including website visitors) can do
Next, the number corresponds to the “what” part of the statement and is a sum of a combination of any these digits:
4Read a file, or read the names of the files in a folder2Write or modify a file, or modify the contents of a folder1Execute or run a file, or access the files in a folder
These digits are the privileges that are assigned to the “who” in the permission mode. Note in the list above that privileges mean something different for files and folders.
Using the correct permission mode is quite important. To better illustrate this, think again of users and roles in WordPress. On a WordPress website, contributors and administrators have different sets of capabilities. Contributors may create new blog posts, but they may not add plugins. Administrators, on the other hand, may add plugins and also create blog posts. Administrators may even change the look of the website if they want to. A clear line separates what users in different roles can do. This is the same with permission modes, except that instead of dealing with blog posts and theme options, we are dealing with files and folders on the server.
Changing Permission Modes
FTP clients usually provide an interface where you can conveniently change the permission mode of your files and folders. Here’s a screenshot of the interface in my FTP client:
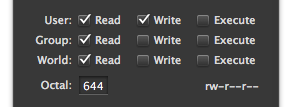
Example of a permission mode interface.
If you have access to your server’s terminal, you can also use the chmod command to change the permission mode of a file or folder:
sudo chmod 644 <file>
To change the permission modes of all files or folders, use chmod in tandem with the find command. For example, you can use this to change all files to 644:
sudo find . -type f -exec chmod 644 {} +
Or use this to change all of your folders to 755:
sudo find . -type d -exec chmod 755 {} +
Refer to “Changing File Permissions in the WordPress Codex” for a guide to changing permission modes.
The Difference Between 644 And 777
Let’s look at some permission modes and how they affect our website.
What would a PHP script with a permission mode of 644 mean? Following the explanation above of how permission modes work, we can decipher what this mode allows users to do with our script:
- The owner’s privileges are “read” (4) + “write” (2) =
6 - The owner’s group privileges are “read” (4) =
4 - Everyone else’s privileges are “read” (4) =
4
In plain language, this means that:
- if we own the script, we may read and modify it;
- everyone else may only read it.
As we can see, 644 is a good permission mode for our PHP script. We can make changes to it, and our Web server can read it.
Now let’s look at folders. What if we owned a folder that had a permission mode of 777? This permission mode can be broken down as follows:
- The owner’s privileges are “read” (4) + “write” (2) + “execute” (1) =
7 - The owner’s group privileges are “read” (4) + “write” (2) + “execute” (1) =
7 - Everyone else’s privileges are “read” (4) + “write” (2) + “execute” (1) =
7
This means that
- anyone may get a list of file names in our folder;
- anyone may create, modify and delete any file in our folder;
- anyone may access the files in our folder.
It is obvious that 777 is a bad permission mode for anything on our WordPress website because any visitor would be able to add files to our directory or even delete scripts. Worse, anyone would be able to put in malicious code and compromise our website.
WordPress Server Configurations
Now we know about permissions and how to read them. But before proceeding to change all of our permissions, we need to understand how our server is set up. Because permissions deal with user accounts and groups, we need to know how our WordPress website runs.
A lot of different server configurations are out there. Different configurations need different sets of permission modes for WordPress to work correctly and securely. We’ll talk about just the two most common configurations and the proper permissions for them:
- Standard server configuration:
- You have a user account.
- Your Web server runs as another user account.
- Shared server configuration or
suEXECconfiguration:- You have a user account.
- Other people who use the server have user accounts and might share the same group with your user account.
- Your Web server runs as the owner of your WordPress files.
The main difference between these two is in how the Web server runs.
Permissions For A Standard WordPress Server Configuration
Standard WordPress configurations require a bit more work than shared server configurations because the Web server has no relationship to our user account.
File And Folder Ownership For WordPress
First, we need to adjust the file and folder ownerships of our WordPress files. We’ll have to make sure of the following:
- that your user account is the owner of all WordPress files and folders,
- that your user account and the Web server’s user account belong to the same group.
To find out the groups that your user account belongs to, you can use this command in your server’s terminal:
groups
Then, to find out the groups that your Web server belongs to, you can temporarily insert this PHP snippet in one of your WordPress scripts:
echo exec( 'groups' );
If your user and the Web server don’t belong to the same group, you can use the following command in the terminal to add your user to one of your Web server’s groups:
sudo usermod -a -G <a-common-group-name> myuser
Lastly, to ensure that everything in our WordPress folder belongs to our user account and has the shared group that we just added, perform this command in your WordPress folder:
sudo find . -exec chown myuser:a-common-group-name {} +
Permissions For WordPress
All of our files and folders should now have the correct ownership. Now it’s time to adjust the permission modes. To make things simpler, you’ll only need to remember the following:
- All files should be
664. - All folders should be
775. wp-config.phpshould be660.
Here’s what we’re trying to achieve with this set of permission modes:
- Our user account may read and modify our files.
- WordPress (via our Web server) may read and modify our scripts.
- WordPress may create, modify or delete files and folders.
- Other people may not see our database credentials in
wp-config.php.
You might be thinking that allowing WordPress full privileges with our folders is not secure. Don’t worry — we’re doing this because WordPress needs certain features to create and modify files. WordPress allows us to upload and remove themes and plugins and even edit scripts and styles from the administrative back end. Without this type of permission, we would have to manually upload themes and plugins every time using FTP.
You can use your FTP client to change the permission modes, or you can use the following commands in your WordPress directory to quickly adjust the permissions of all of your files and folders:
sudo find . -type f -exec chmod 664 {} +
sudo find . -type d -exec chmod 775 {} +
sudo chmod 660 wp-config.php
Note that some Web servers are stricter than others. If yours is strict, then setting your wp-config.php to 660 might stop your website from working. In this case, just leave it as 664.
Permissions For A Shared Server Configuration Or SuEXEC Configuration
Permissions for shared server configurations are easier to implement. We won’t dwell on ownership because the Web server runs as the owner of our files and folders. Because our user account and the Web server share the same permissions (both are owners), we can dive right into modifying the permission modes:
- All files should be
644. - All folders should be
755. wp-config.phpshould be600.
Similar to the previous set of permission modes, these break down as follows:
- Our user account may read and modify our files.
- WordPress (via our Web server and as the account owner) may read and modify our scripts.
- WordPress may create, modify or delete files or folders.
- Other people may not see our database credentials in
wp-config.php.
Again, you can use an FTP client to change the permission modes, or you can use the following commands in your WordPress directory to quickly adjust the permissions of all of your files and folders:
sudo find . -type f -exec chmod 644 {} +
sudo find . -type d -exec chmod 755 {} +
sudo chmod 600 wp-config.php
Similar to the standard WordPress server configuration, your server might be stricter than others and might not allow wp-config.php to be 600. In this case, you can adjust it to a more lenient 640; if that still doesn’t work, then use 644.
Always follow these guidelines and your WordPress files should be kept safe from intruders.
Common Pitfalls
A common mistake people make is to set the uploads folder to 777. Some do this because they get an error when trying to upload an image to their website, and 777 quickly fixes this problem. But never give unlimited access to everyone, or else you’ll make the Web server vulnerable to attack. If you follow the guidelines covered in this article, then you should have no problems uploading files to your website.
At times, though, a plugin will request that you set a file to 777. On these occasions, you can temporarily set it to 777, but make sure to set it back to its original permission mode when you’re done.
Conclusion
We’ve learned now about the proper permissions and file ownership of a WordPress website. We’ve also learned to avoid a permission mode of 777 because of how it endangers the Web server.
Hopefully, you can implement these tips to keep your WordPress website safe and secure. If you have any additional tips regarding permissions and security, please share them in the comments below.
Excerpt image credit: Christopher Ross
Further Reading
- What To Do When Your Website Goes Down
- How To Keep Your Coding Workflow Organized
- How to find out why your website stopped working
- 9 Steps To A Happy Relationship With Your Hosting Provider


 Flexible CMS. Headless & API 1st
Flexible CMS. Headless & API 1st





